Table of Contents
Table of Contents
This is what SERP APIs do! They access search results and organize the data, like keywords and rankings, which is useful for things like marketing and tracking how your company appears in searches. Learn more about SERP API endpoints.
But just like any powerful tool, SERP APIs need protection. Hackers could try to steal information or mess with the data. This guide will teach you how to keep your SERP API safe and your business protected.
Why Secure Your SERP API Endpoints?
Here are some compelling reasons to prioritize the security of your SERP API endpoints:
Data Protection: SERP data can reveal valuable insights into user behaviour, search trends, and competitor strategies. A security breach could expose this sensitive information to unauthorized parties, leading to a competitive disadvantage.
Maintaining Trust: If your SERP Scraper API is compromised and used to manipulate search results, it can erode user trust in your brand and the data you collect.
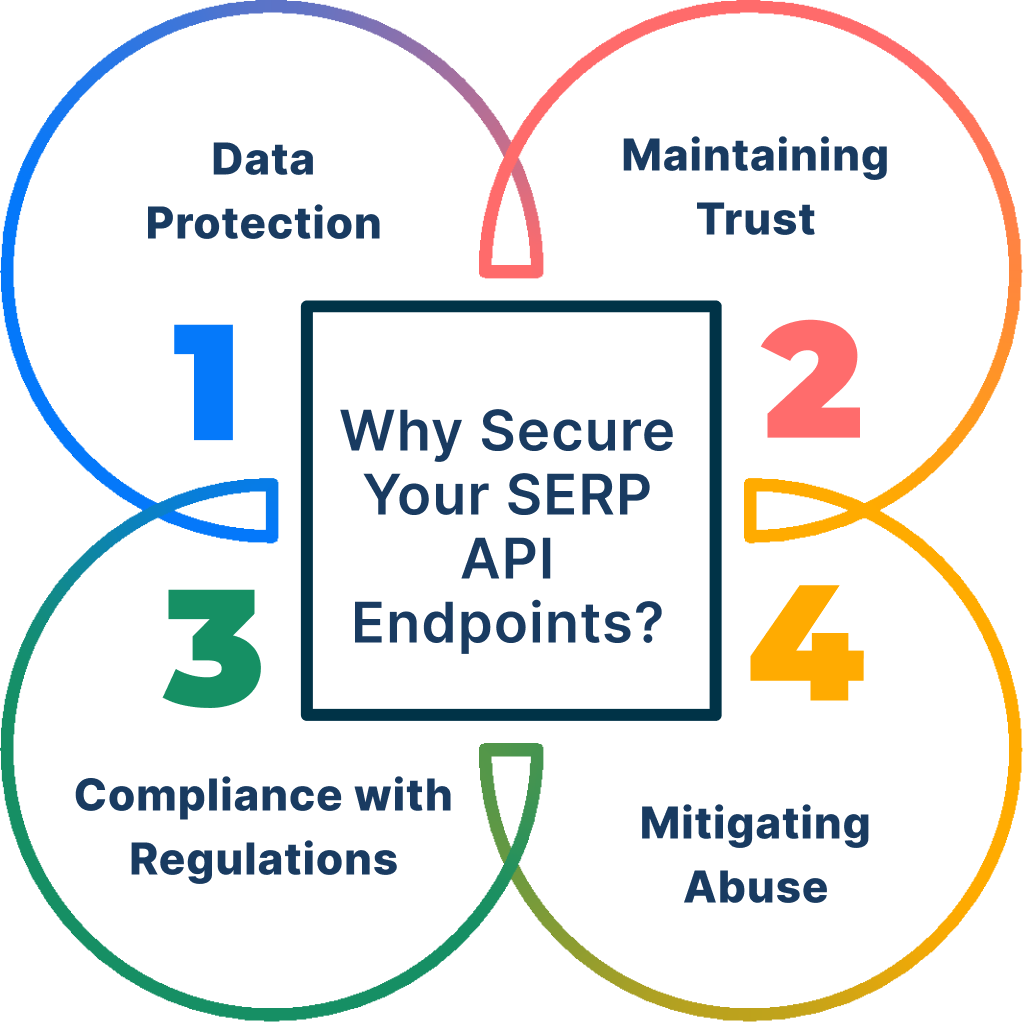
Mitigating Abuse: Unsecured SERP APIs are susceptible to automated attacks, such as scraping or spamming, which can overwhelm your systems and incur additional costs.
Compliance with Regulations: Data privacy regulations may mandate specific security measures for handling SERP API data.
Common Threats to SERP API Endpoints
Here’s a look at some of the most common threats that can target your SERP API endpoints:
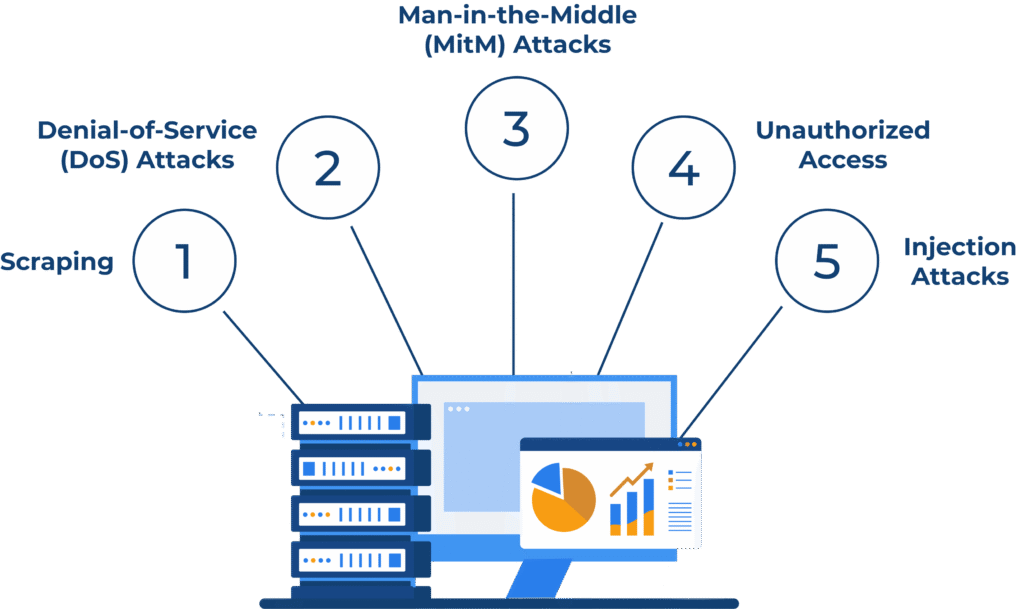
- Scraping: Attackers can use automated scripts to scrape large amounts of data from your SERP API, overwhelming your systems and potentially violating terms of service with search engine providers.
- Denial-of-Service (DoS) Attacks: A flood of requests can be directed at your API endpoint, rendering it unavailable to legitimate users.
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept communication between your application and the SERP API, potentially stealing data or injecting malicious code.
- Unauthorized Access: Hackers might exploit vulnerabilities in your API authentication mechanisms to gain unauthorized access to sensitive data.
- Injection Attacks: Malicious code can be injected into API requests, potentially compromising your systems or manipulating data.
Best Practices for Securing Your SERP API Endpoints
By implementing the following best practices, you can significantly improve the security posture of your SERP API endpoints:
- Double-check who uses it: Make sure only authorized users can access your data, like using a secret key.
- Limit how much data they can take: Stop overwhelming attacks by controlling how often users can request information.
- Inspect what they send: Check all incoming data for hidden tricks that could steal information.
- Scramble sensitive info: Encrypt data to make it unreadable even if someone gets hold of it.
- Regular check-ups: Have your API reviewed by security experts to find and fix any weaknesses.
- Stay on top of things: Keep your API software updated with the latest security fixes.
Additional Considerations for Enhanced Security

Here are some additional measures you can take to further strengthen your SERP API security:
- IP Address Filtering: Restrict access to your API from specific IP addresses or IP ranges to mitigate unauthorized access attempts.
- Monitoring and Logging: Implement comprehensive monitoring and logging solutions to track API activity and identify suspicious behaviour. This will help you detect and respond to security incidents promptly.
- Web Application Firewall (WAF): Consider deploying a WAF to filter incoming traffic and block malicious requests before they reach your API endpoint.
References and Further Reading
For a deeper dive into SERP API security, consider referring to the following resources:
OWASP API Security Top 10: This industry-standard guide outlines the top 10 security risks faced by APIs and provides recommendations for mitigation.
Securing Your Web Services: This comprehensive guide delves into web service security best practices, many of which apply to SERP APIs as well.
Google Search API Documentation: SERP API docs might not directly cover security, but they can reveal areas where security risks might exist.
Industry-Specific Security Regulations (e.g., GDPR, CCPA): Data privacy rules like GDPR may apply to your SERP API. Check official sites for details on how to comply.
Conclusion
By following the best practices outlined in this guide and staying vigilant about potential threats, you can effectively secure your SERP API endpoints. Remember, security is an ongoing process, and it’s crucial to continuously monitor, update, and adapt your security posture as new threats emerge.
A secure SERP API not only safeguards your valuable data but also fosters trust with users and ensures the integrity of the insights you glean from search results. By taking a proactive approach to security, you can empower your business to leverage the power of SERP APIs with confidence.